#24 - CyberArk Privilege Cloud ISPSS Architecture Explained
In this video, you’ll explore the CyberArk ISPSS Privilege Cloud architecture. You’ll learn how all the components work together to secure privileged access and enhance your organization’s security. Whether you’re an IT professional, security engineer, or just curious about CyberArk, this video will give you a clear understanding of ISPSS and its role in Privilege Cloud.
CyberArk Docs
CyberArk docs Privilege Cloud Architecture has a detailed description of all the components.
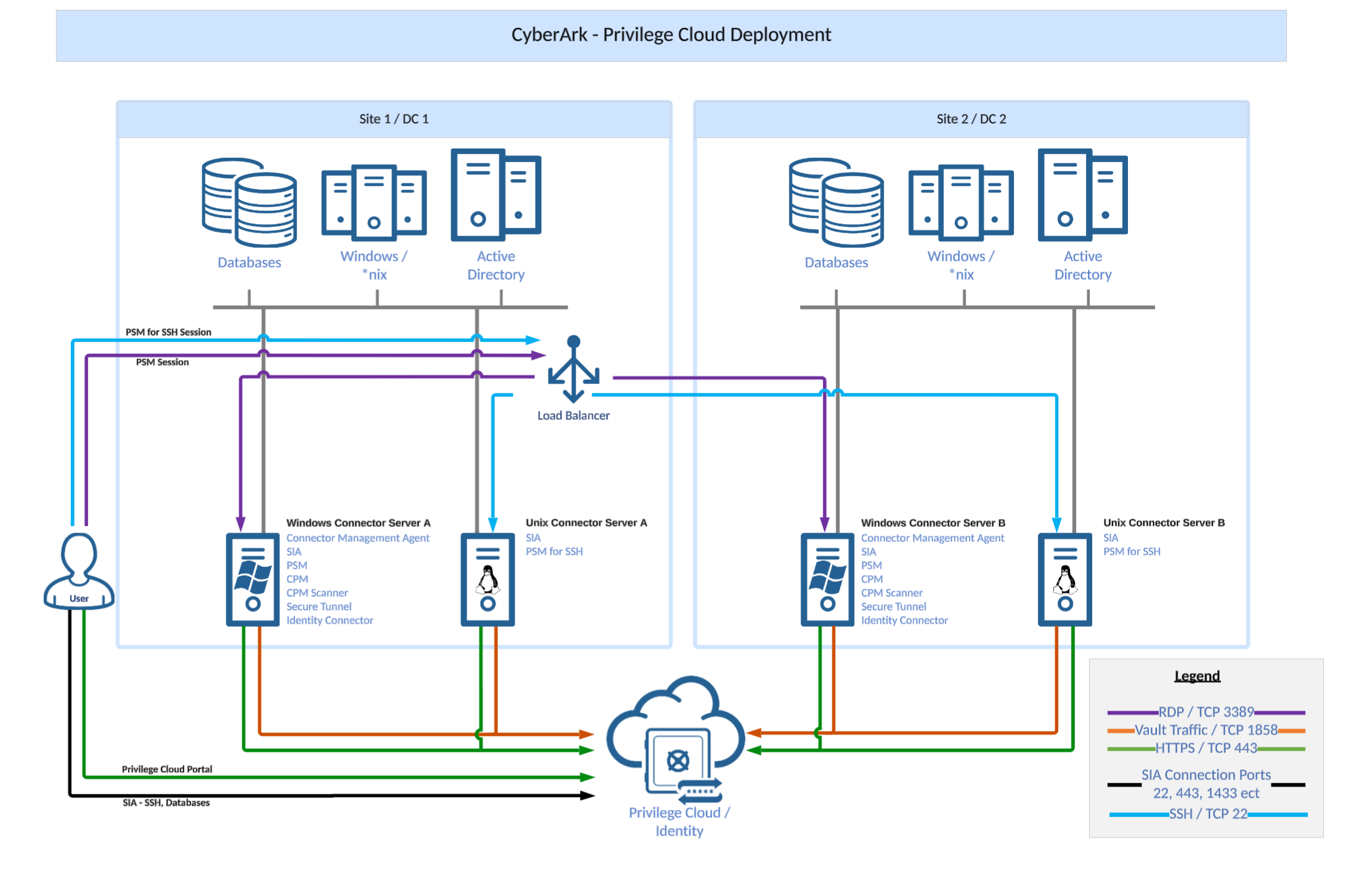
High-Level Architecture Diagram
The below diagram is a high level overview on how a typical environment will connecto to CyberArk Privilege Cloud ISPSS.
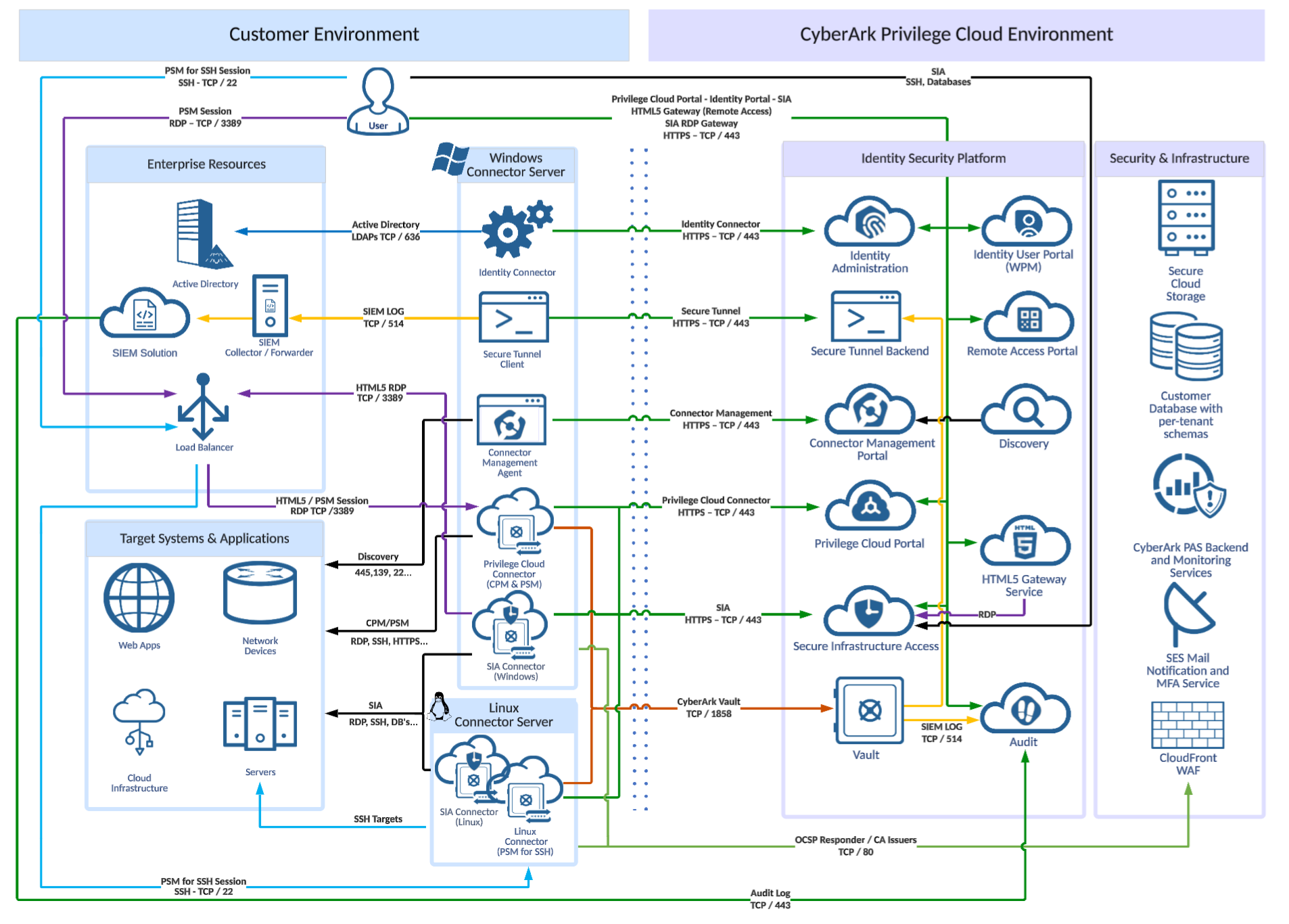
Low-Level Architecture Diagram
This low-level diagram is an example scenario where Active-Directory is the source for identities.
This low-level diagram is an example scenario where an external IdP is the source for identities. 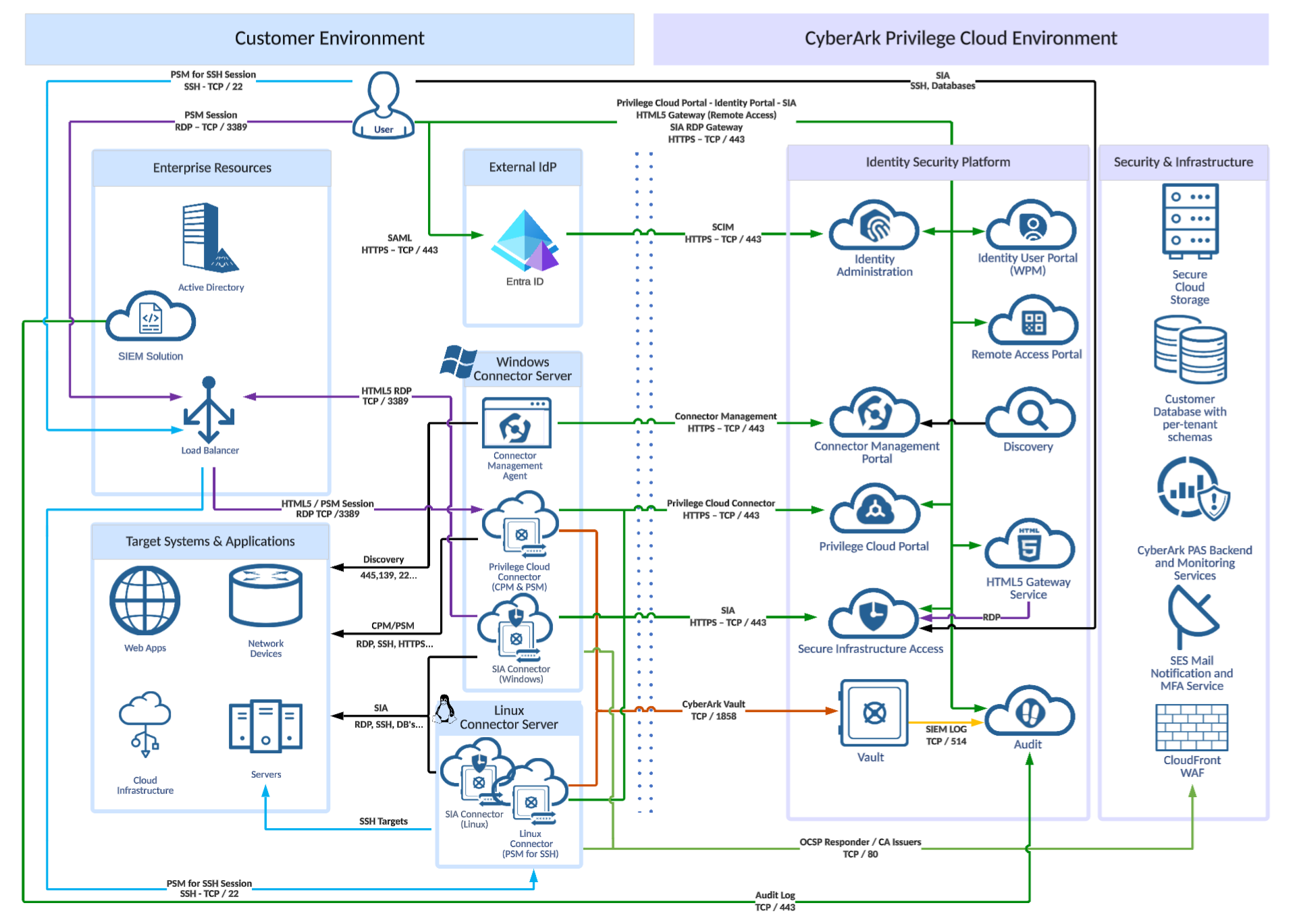
Objectives:
- High-level deployment overview
- Low-level architecture components
Timeline:
- Intro 0:00
LinkedIn: https://au.linkedin.com/in/bradmcdowell
#IIS #WIN-ACME #Cloudflare #Letsencrypt